Military and Defense
Supporting the Department of Defense, UK MOD, and other NATO partner forces for over 25 years.

Full-spectrum intelligence analysis for a wide range of military use cases
Deriving intelligence across multiple information feeds can be challenging. This is often compounded with the need to synchronise headquarter operations to those working on operations.
i2 delivers a scalable environment to collate information from SIGINT, HUMINT, OSINT, SOCINT, GEOINT, and sensor data with the capabilities to perform all-source multi-dimensional analysis and reporting. With a modular and interoperable approach, i2 provides the agility and self-service requirements to combat today’s complex and changing landscape.

Counter-Terrorism
Prevent, mitigate, and respond to terrorist threats

Counter-Insurgency
Defeating irregular forces such has guerrillas and revolutionaries

Counter-Intelligence
Respond to espionage and intelligence activities by foreign entities

Force Protection
Safeguarding military personnel, equipment, facilities, and operations

Cyber Threat-Hunting
Proactive search and mitigation of potential cyberattacks and vulnerabilities

Conventional Order-of-Battle Analytics
Assessment of a military forces' capabilities in conventional operations

Military Law Enforcement
Enforcing military laws and regulations

Supply Chain Analysis
Assessment of the logistics and distribution network
i2 is a key component of military intelligence
-
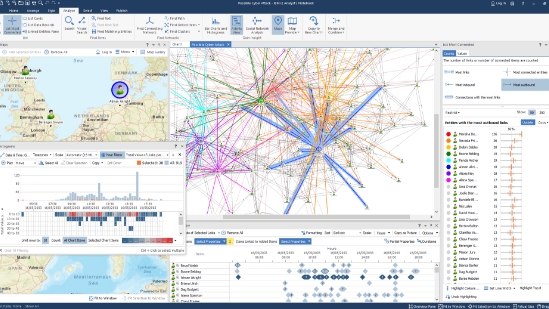
i2 Analyst’s Notebook’s rich functionality has been successfully deployed in numerous military use cases. From detailed of pattern-of-life to precise temporal analysis it has enabled both the protection of allied forces and the identification of hostile actors.
More advanced solutions such as Analysis Hub and Analysis Studio have enhanced the stand-alone capability into a fully integrated solution with a shared data repository, connectors to numerous data streams, as well as tight integration with ESRI Arc-GIS, and other partner platforms, making i2 a powerhouse for data analysis.
-
And with i2 TextChart we are vastly reducing the analyst’s workload. It is pioneering the automation of extracting entities, links and properties from unstructured text from OSINT as well as traditional intelligence reports.
As the military shifts from mainly counter-insurgency and counter-terrorism to confront more conventional near-peer adversary threats, we have made the requisite changes to our use case model to enable customers to fuse data from disparate sources, locate and visualize enemy troop movements, and help predict outcomes. No longer merely a law-enforcement style tool for link analysis but an open-architecture, customizable solution for full-spectrum intelligence analysis.
-
Analysis Hub for National Security
Do you have large and overwhelming data sets to analyze? With its scalable, extensible design, Analysis Hub helps organizations overcome information overload and perform intelligence analysis and analytics — at scale and at speed.