Proudly supporting countries' forces around the world for over 25 years.
Deriving actionable intelligence from multiple information feeds can be a daunting task, especially when synchronizing headquarters operations with field units.
i2 Group solutions offer a scalable environment that integrates information from your data corpuses, multi-source Intelligence, and sensor data. It enables both synchronous and asynchronous operations across all warfare domains, providing capabilities for all-source, multi-dimensional analysis and reporting. With its modular and interoperable design, i2 ensures agility and self-service functionality, empowering military forces to effectively navigate today’s complex and evolving operational landscape
Organizations Globally
NATO Member States
FVEY Collaborators
Defense Use Cases Supported
i2 Overwatch provides real-time interactive mapping, with NATO-compliant symbology. Synchronized network and geospatial views provide comprehensive battlefield visibility.
i2 operates as a standalone capability or integrates seamlessly with systems like Battle Management Systems, Geospatial Platforms, ISR capabilities, and Military Staff Process Management systems.
Empower i2 staff to create critical products such as MCOO, IPMB/IPB, and OCOKA with ease.
i2 excels in 'Grey-Zone' intelligence assessments by querying both conventional military data and commercial services.
Overlay enemy doctrine with evolving intelligence data on a strong geospatial platform, utilising i2’s event and time analysis capabilities.

Empower the J2, 3 & 5 functions to collaborate around an i2 enabled Battlespace Object Management System.
Deploy forward with a fully functioning i2 solution, enabling disconnected analysis from static enterprise systems, adaptable for both field and barracks environments.
i2 queries multiple secure data sources continuously or ad-hoc, acting as a centralised data store or in a hybrid model.
i2’s open design allows for deployment, management, and modification by organic military staff, ensuring operational certainty during high tempo periods.
Prevent, mitigate, and respond to terrorist threats
Defeating irregular forces such as guerrillas and revolutionaries.
Respond to espionage and intelligence activities by foreign entities.
Safeguarding military personnel, equipment, facilities, and operations.
Proactive search and mitigation of potential cyberattacks and vulnerabilities.
Assessment of a military forces' capabilities in conventional operations.
Enforcing military laws and regulations.
Assessment of the logistics and distribution network.
i2 Analyst’s Notebook’s rich functionality has been successfully deployed in numerous military use cases. From detailed of pattern-of-life to precise temporal analysis it has enabled both the protection of allied forces and the identification of hostile actors.
More advanced solutions such as Analysis Hub and Analysis Studio have enhanced the stand-alone capability into a fully integrated solution with a shared data repository, connectors to numerous data streams, as well as tight integration with ESRI Arc-GIS, and other partner platforms, making i2 a powerhouse for data analysis.
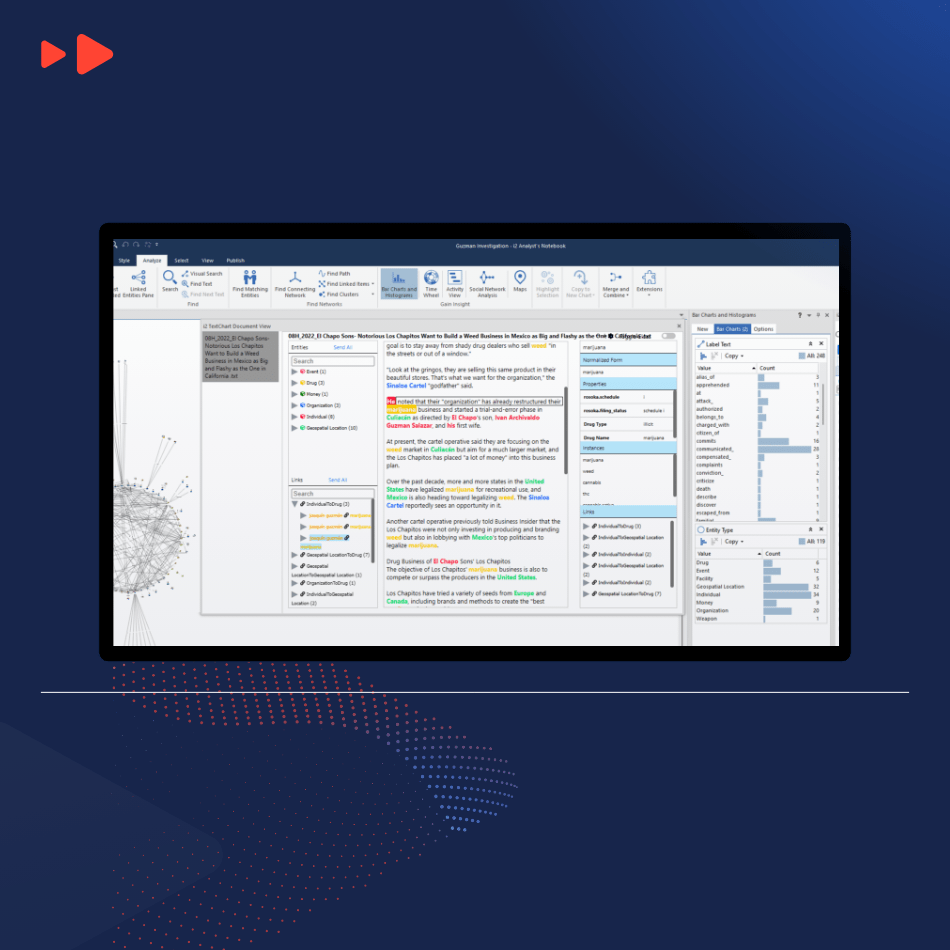
With i2 TextChart we are vastly reducing the analyst’s workload. It is pioneering the automation of extracting entities, links and properties from unstructured text from OSINT as well as traditional intelligence reports.






i2 Overwatch is a single platform for collecting, analyzing and visualizing mission-critical intelligence - built to meet the needs of modern military operations.
i2 Analyst’s Notebook’s rich functionality has been successfully deployed in numerous military use cases. From detailed of pattern-of-life to precise temporal analysis it has enabled both the protection of allied forces and the identification of hostile actors.
More advanced solutions such as Analysis Hub and Analysis Studio have enhanced the stand-alone capability into a fully integrated solution with a shared data repository, connectors to numerous data streams, as well as tight integration with ESRI Arc-GIS, and other partner platforms, making i2 a powerhouse for data analysis.
With i2 TextChart we are vastly reducing the analyst’s workload. It is pioneering the automation of extracting entities, links and properties from unstructured text from OSINT as well as traditional intelligence reports.



© 2026 i2 Group / N. Harris Computer Corporation. All trademarks owned by N. Harris Computer Corporation.
1 Cambridge Square, Milton Avenue, Cambridge, CB4 0AE, UK