i2 Analyst's Notebook allowed the INTERPOL General Secretariat to visualize large amounts of data to link and ultimately catch members of an organised jewlellery gang called the Pink Panthers.
INTERPOL's Pink Panthers Project tracked a number of seemingly isolated armed jewellery robberies committed in Japan, Spain, Dubai, Switzerland, Cyprus, and France that started in 2002.
A breakthrough came following a DNA match on INTERPOL databases, linking a suspect to three different cases and a picture of the criminal network began to emerge. The offenders, all originating from the former Yugoslavia, robbed high-value jewellery stores across the world, before immediately leaving the targetted country.
The Rules of Processing Information (RPI), the legal framework that controls information sharing at INTERPOL, requires criminal information to be recorded so that it is possible to identify the county of origin of specific information in order to safeguard its sharing. For one particular offender recorded in the PINK PANTHERS Project, INTERPOL had received different information from eight member countries including a DNA profile, fingerprints, photos, aliases, and possible links to ten other cases. However, the aliases or photos sent by one country may or may not be the same as those sent by another.
When the INTERPOL Criminal Information System (ICIS) database was queried for this particular offender using i2 Analyst’s Notebook, the extraction result showed eight people with the same first name, last name, and date of birth. These all referred to the same person, with each entity on the chart being a “clone” of the person - one each, from each of the eight member countries that provided data. There were more than 400 individuals linked to the PINK PANTHERS Project, with the "cloning" issue being the same for many other suspects.
When these clones were expanded, even to only a first-degree expansion, to see further cases, aliases, and accomplices they are linked to, the result posed a significant challenge from an analytical perspective.
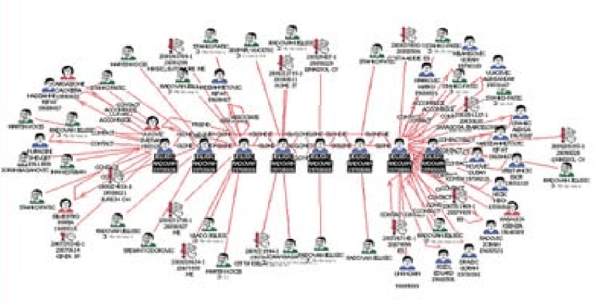
Clones of entities as a result of data from different sources
To tackle this problem, after expanding all the clones’ links, the analysts used the Merge Entities tool to collapse all clones into one. This allowed the visualisation of all relevant data linked to a suspect to be viewed at once, enabling the analysts to deal more efficiently with the information.
This enhanced visualization of the vast amounts of data coming from different countries allowed the analysts to identify key links between suspects and associates, and connect several of the same suspects to different crime scenes.
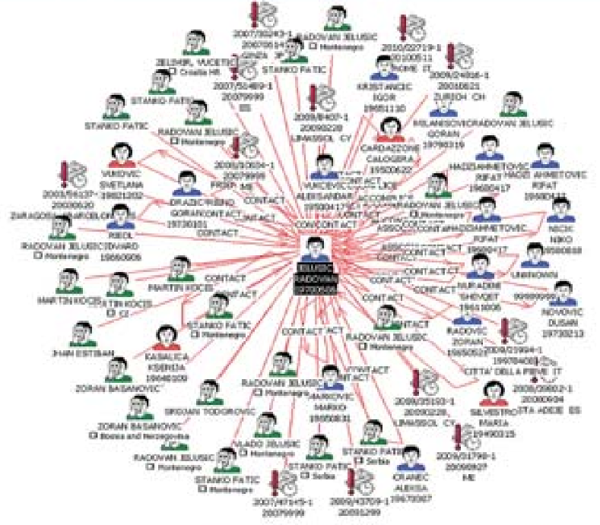
An entity merged, showing all its connections
i2 Analyst’s Notebook and iBridge allowed INTERPOL to deal with large amounts of data in a more efficient way.
The PINK PANTHER’s suspect-related information in the ICIS database remains unchanged (complying with the rules for the processing of information) and the visualization of the data for analytical purposes was significantly improved. Due to the large amount of nominal information sent to INTERPOL in the framework of this project, analysing the data by hand would have been an impossible task.
Once in a position to identify how each individual is linked to each case in each country and who their aliases and accomplices were, analysts and investigators had a better understanding of the criminal network and the crime phenomenon, thereby being able to identify additional leads as well as information gaps.
Find out more about i2 Analyst's Notebook, or contact us to see how we can help you with OCG and law enforcement investigations.



© 2026 i2 Group / N. Harris Computer Corporation. All trademarks owned by N. Harris Computer Corporation.
1 Cambridge Square, Milton Avenue, Cambridge, CB4 0AE, UK